Quizlet What Is The Size In Bits Of A Register In The Risc-v Architecture?
This commodity aims to give the reader a detailed understanding of the RISC-V Architecture and will likewise assist in comparing the RISC-V architecture with popular ARM compages. Before nosotros dive into technical terminologies and get-go comparing the two architectures, it is important for the reader to understand what is meant past Instruction Set Architecture.
Instruction Set Compages (ISA) is basically the portion of the machine that is visible to the assembly level programmer or the compiler author. ISA is where software meets hardware. ISA defines the commands/ instructions that can natively be understood by a auto and its micro-architecture, and it as well defines how the instructions are to be stored, accessed, and implemented.
We give instructions to the hardware of the computer using a linguistic communication that a figurer tin understand. The computer linguistic communication is made up of the words called instructions and the vocabulary is called an instruction set . Instruction sets tell united states of america about the function of each instruction and how the instruction is represented in memory (encoding).
The term architecture describes the functional specification of a processor. Information technology describes what functionality the software can rely on the hardware to provide. Architecture does not tell yous how a processor is congenital. It tells you lot what a processor can do. Micro-architecture on the other hand describes how a processor is built and designed. Micro-architecture defines, the number and size of caches, cycle counts of instructions, pipeline length, and more.
Having understood what ISA is, nosotros now move on to give an overview of RISC-Five and ARM architecture.
RISC-Five Architecture Overview
RISC-V (pronounced "risk-five"), is an open up ISA that is freely available to academia and industry. It builds and improves upon the original Reduced Instruction Set (RISC) Architecture.

RISC-Five is the fifth edition of the RISC ISA designs from UC Berkeley. The roman numeral "V" signifies "variations" and "vectors" to support a range of computer architecture research.
Features of RISC-5 Architecture
- RISC-V is a load-shop architecture, meaning three things: (i) Its arithmetic instructions operate only on registers, (two) Simply load and store instructions transfer data to and from retentiveness, and (iii) Data must first be loaded into a register before it can be operated on.
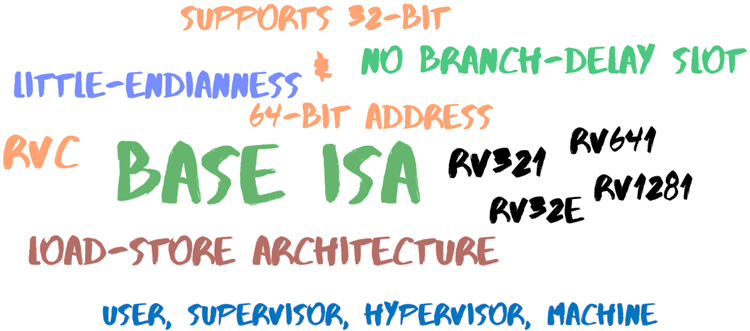
- RISC-V is non over-architectured/over-optimized for any particular implementation, micro-architectural pattern, or deployment target and hence it is suitable for all computing purposes. It is able to do this because its ISA is cleaved downward into two parts, the base ISA and optional extensions. The base ISA is restricted to contain a minimal set of instructions that are enough to form a compiler target and to satisfy the mod operating systems. The base ISA cannot exist re-divers and it is present in any implementation.
- There are boosted ISA extensions that tin exist added to the base ISA depending on the implementation. This allows the RISC-V to also support all-encompassing customization and specialization.
- It is the smallest ISA for 32-chip and 64-chip addresses and uses fiddling-endian byte ordering for the memory arrangement. Piffling-endian byte ordering ways the least significant byte of multi-byte data is stored at the everyman memory address. The LSB is stored first.
- RISC-V uses RVC (RISC-V code compression) technique to improve the program lawmaking size and too reduces the number of CPU cycles per instruction at the cost of increasing the number of instructions per plan. It sacrifices code density to simplify the implementation circuitry.
- RISC results in large code sizes that are not optimum, peculiarly for embedded systems because they accept a limited instruction memory capacities. To reduce the code size, RISC-Five uses its RVC extension. RVC substitutes the common 32-bit instructions with shorter 16-bit instruction encodings. Information technology also has no branch delay slot.
ARM Architecture Overview
ARM originally stands for Acorn RISC Machine but it was later inverse to Advanced RISC Machine. Information technology is arguably, the most unremarkably used processor compages in the earth.

Information technology was kickoff developed by a reckoner manufacturer called Acorn Computers in the belatedly 1980s for its personal computers. It is a blazon of RISC architecture. In that location are iii different types of Arm architectures for different applications. They are A, R, and Yard architectures.
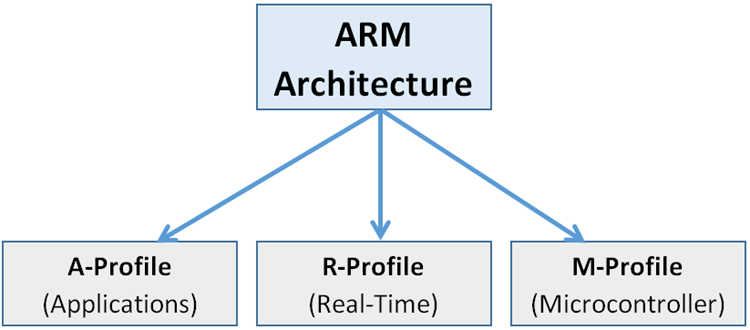
A-Profile (Applications): Optimized to run complex operating systems such as Windows and Linux. It offers the highest performance.
R-Profile (Real-Fourth dimension): Optimized for systems with real-time constraints such every bit embedded control systems.
Chiliad-Profile (Microcontroller): Optimized for low-power devices and is used by many IoT devices
Features of Arm Architecture
- It is a load-store architecture with a 32-scrap addressing range.
- Unlike RISC-V, it is non an open-source ISA but a proprietary ISA.
- It uses bi-endian byte-ordering for the memory system. This means an arm processor/motorcar is able to compute/pass data in both endian formats at a hardware level.
- It uses the Thumb instruction set up to reduce the program code size. Thumb is also known as the T32 educational activity ready, it is used in pre-Armv8 processors.
- It is a mixture of 32-bit and 16-scrap length teaching prepare which has an optimum lawmaking density for systems with a retentivity size and cost constraint like embedded applications. It provides the high performance of a 32-fleck instruction set up and it nigh provides the code density of a 16-bit instruction set.
RISC-V vs ARM
Now that nosotros have an insight on ISA, RISC-V, and ARM, we will compare the two side-past-side based on a diversity of factors.
| Property | RISC-5 architecture | ARM architecture |
| Licencing | Open-source | Proprietary |
| RISC Compages | ✓ | ✓ |
| Load-store architecture | ✓ | ✓ |
| Back up 32-bit and 64-scrap accost spaces | ✓ | ✓ |
| Default Endianness | Footling-endian | Bi-endian |
| Code Compression Techniques | ✓(RVC) | ✓(Pollex) |
| Branch delay slot | none | none |
Why is RISC-V Considered a Threat to the ARM Architecture?
First of all, RISC-V is open up-source while ARM is non. This means that RISC-V is license-free and royalty-costless. RISC-V allows the user to extend the ISA with new instructions and innovate the micro-compages of the RISC-V processors for costless only ARM asks the user to pay royalty-fees. This fabricated RISC-V quickly welcomed by many manufacturers.

In terms of complexity, ARM is considered to be more than complex than RISC-V. The other reason is that ARM is more over-optimized for mobile-phones than information technology is for laptops, desktops, and servers. RISC-V is not over-optimized for one particular implementation. It is suitable for all computing systems, from microcontrollers to supercomputers.
Summary
RISC-5 and ARM are both RISC ISA Architectures. The former is open-source while the latter is a proprietary ISA. This article outset covered the meaning of ISA past breaking down the term into Education, Instruction Ready, Architecture and describing each of the individual words. Both RISC-V and ARM have their ain advantages and it hard to take a side, merely the flexibility and open-source nature of RISC-5 has made it possible to be adopted faster into the electronics manufacture, promising a potential future!
Quizlet What Is The Size In Bits Of A Register In The Risc-v Architecture?,
Source: https://circuitdigest.com/article/understanding-risc-v-architecture-and-why-it-could-be-a-replacement-for-arm
Posted by: withrowgovers.blogspot.com


0 Response to "Quizlet What Is The Size In Bits Of A Register In The Risc-v Architecture?"
Post a Comment